Installing Mathematica for OS/2 Symmetrical Multiprocessing (SMP) v2.11 / HPFS386 Hack in VirtualBox
(Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size.)
Procedure to install Mathematica v2.2 for OS/2 in my local copy of the VirtualBox 7.0.12 OS/2 for SMP v2.11 with HPFS386 virtual machine hosted in my four(4) CPU / eight(8) CORE Metztli Reiser4 development environment.
Subsequently this VirtualBox vm will be uploaded to a remote server, with a Metztli Reiser4 for AMD CPUs environment, i.e., reizer4, and I will utilize VBoxManage to increase the cpu count to 16 in the headless environment.
Although the visual media is self explanatory, I included a few Mathematica for OS/2 installation procedure snapshots which may be of relevant historical interest:
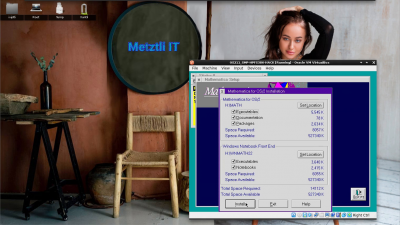
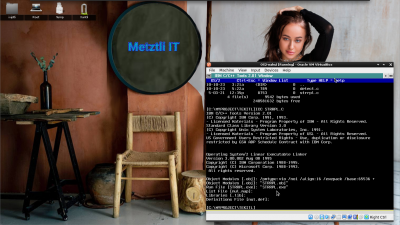
Diskette 1 has been inserted a priori and we can see that it is executing initial installation phase:
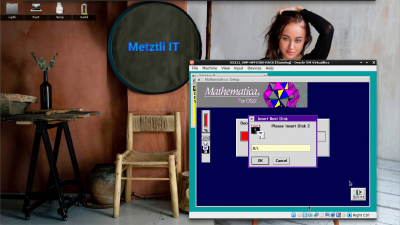
Mathematica for OS/2 installer prompts for diskette 2:
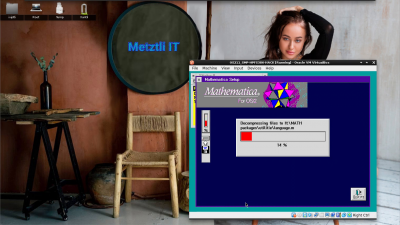
Diskette 2 installer executes and proceeds with second phase of installation:
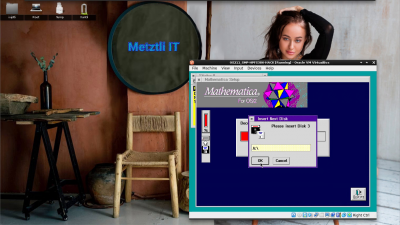
Mathematica for OS/2 installation routine prompts for diskette 3:
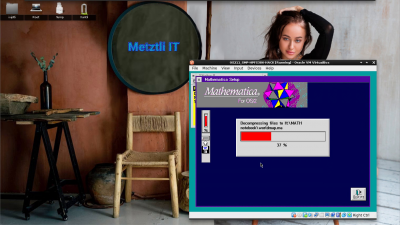
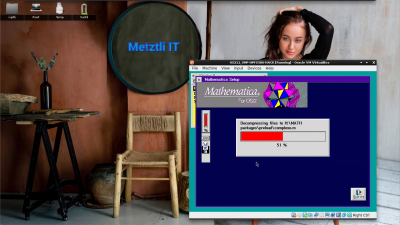
Diskette 3 routine of the installer picks up where the previous left of:
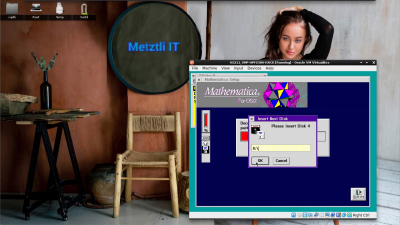
Mathematica for OS/2 installer routine prompts for diskette 4:
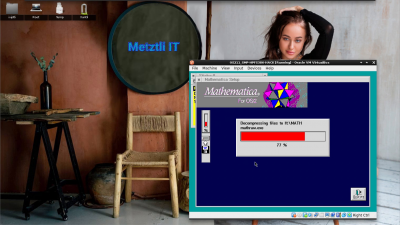
Diskette 4 carries installation past the half of the total routine:
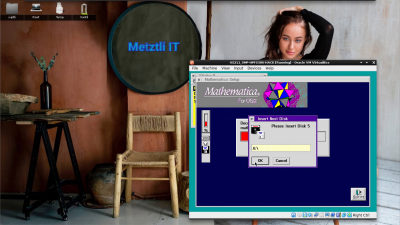
Mathematica for OS/2 installer prompts for the final diskette 5:
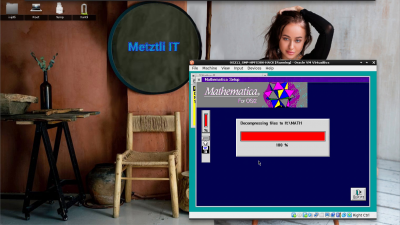
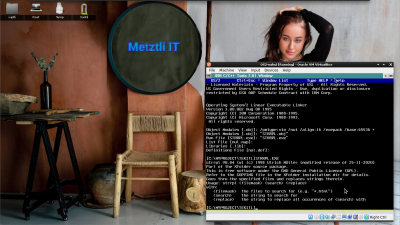
Diskette 5 installation routine completes the Mathematica for OS/2 installation:
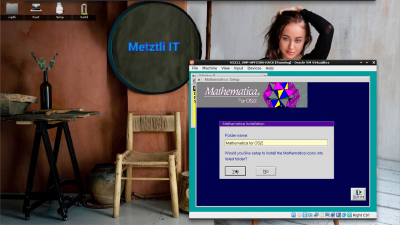
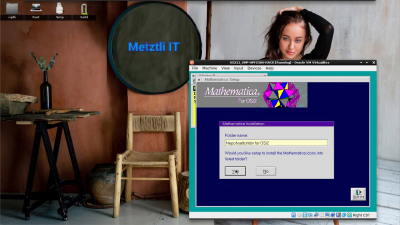
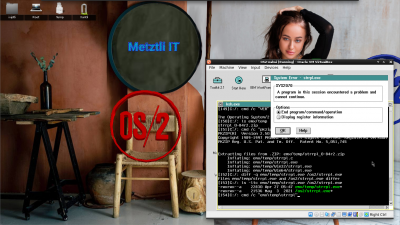
Mathematica for OS/2 prompts us whether we agree with the default -named folder...
Or else ![]()
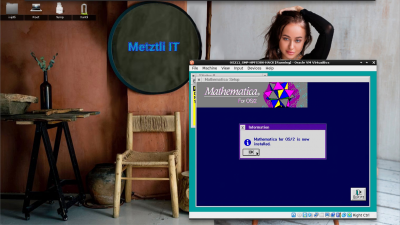
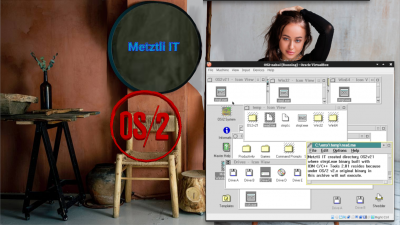
Subsequently, a dialog informs us that Mathematica for OS/2 is installed!
Nepohualtzintzin (Ne∙pohual∙tzin∙tzin) ≈ I can compute infinitesimals -- from the Nahuatl, real Mexico - Tenochtitlan's language -- which predates the alien Anglo-Saxons / Iberian / French, etc. all, European invaders' vulgar Latin -derived dialects on this stolen continent originally known as Ixachitlan ≈ Landmass Immensity.
OS/2 for Symmetric Multiprocessing (SMP) 16 CPU/Core version 2.11 with Mathematica: 'Klein Bottle'
Mathematica for OS/2 2.11 on SMP: 'Klein Bottle'
As an addendum to my previous 'Mathematica on OS/2 Symmetrical Multiprocessing (SMP) for v2.11 Guest in VirtualBox 16 CPU/Cores' post in Collection Ixiptli, I remembered I had seen the so-called 'Klein Bottle' in an older manual I had many Metztli ago.1
(Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size.)
1 Notwithstanding, at that time, the front window of my car was broken and my backpack was stolen in San Francisco as I had parked, on the street, next to San Francisco State University -- and I had that manual in there.
OS/2 2.11 SMP Bootable CDROM 10 Minute Installation Hack into VirtualBox
There was, still is, something appealing about OS/2 -- it was ahead of its time, Warp indeed -- The Integrating Platform. I came across some relevant resources and created an OS/2 2.11 Bootable CDROM media for VirtualBox -- as I heard, through the grapevine, that it was undoable. ![]()
Many moons ago, huehue Metztlapohualli, i.e., 'in the ancient month count', OS/2 enabled me to learn Unix by utilizing the GNU/Linux utilities ported by OS/2 hackers. Accordingly, once IBM orphaned the OS/2 -- and the executives even balked at our multiple petitions to have the OS open sourced -- the transition to Linux was relatively painless. As a matter of fact, while creating this hack I had to bring my old ported GNU/Linux utilities, alternating between OS/2 2.0, 2.1x, and even Warp 3, environments so as to alleviate the shortcoming of 640x480 resolution.
Due to the scarcity of information, I usually operate by inductive reasoning. Notwithstanding, I came across the following 'nugget':
OS/2 has supported SMP for quite a while in special editions of OS/2. The first version was 'OS/2 2.11 for Symmetrical Multiprocessing'...
The diffences between the single-processor OS/2 and the SMP version are very small: 2 APIs for controlling the CPUs, an extra index for DosQuerySysInfo() and 4 APIs for dealing with spinlocks. I know that the 'SMP addendum' mentions a lot of other things, but they are server things, not SMP things.
'OS/2 2.11 SMP' supports up to 16 processors,...1
Yet my build of VirtualBox, from source, under a Metztli Reiser4 Debian environment can only go up to 8 processors/cores and ![]() higher resolution than 640x480...
higher resolution than 640x480...
Update 12-18-2022 : my personal development computing environment can only go up to eight(8) cores; however, I installed another Oracle VirtualBox 7.0.4 -- although 'headless' -- in one of my remote Metztli Reiser4 servers. I made use of VNC to make connection and although Remmina experience a buggy pointer (or mouse) I was able to bring up the SMP Monitor. I could not delay this event as it is not everyday that an OS/2 for Symmetrical Multiprocessing (SMP) Version 2.11 is seen running on 16 CPU/Cores!
OS/2 for SMP Version 2.11 remote instance accessed via VNC
CONVERT FROM 2.1 BASE VIDEO INTO 3.0 BASE VIDEO IN ORDER TO TAKE ADVANTAGE OF THE MONITOR CONFIGURATION FEATURE OF THE 3.0 SYSTEM ICON
At our OS/2 2.1x CMD, executing the following:
Shell
\OS2\VCFGINST.EXE |
the screen will momentarily blank; subsequently, shutting down and then rebooting our OS/2 2.1x then, opening the Screen object will show the current screen resolution enabled by the conversion into 3.0 Base Video:
(Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size. Alternatively, the video with larger screen size may be shown in the Calli, i.e., 'Home', collection front page)
"
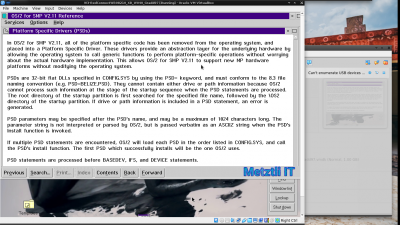
Platform Specific Drivers (PSDs)
In OS/2 for SMP V2.11, all of the platform specific code has been removed from the operating system, and placed into a Platform Specific Driver. These drivers provide an abstraction layer for the underlying hardware by allowing the operating system to call generic functions to perform platform-specific operations without worrying about the actual hardware implementation. This allows OS/2 for SMP V2.11 to support new MP hardware platforms without modifying the operating system.
PSDs are 32-bit flat DLLs specified in CONFIG.SYS by using the PSD= keyword, and must conform to the 8.3 file naming convention (e.g. PSD=TENOCHCA.PSD). They cannot contain either drive or path information because OS/2 cannot process such information at the stage of the startup sequence when the PSD statements are processed. The root directory of the startup partition is first searched for the specified file name, followed by the \OS2 directory of the startup partition. If drive or path information is included in a PSD statement, an error is generated.
PSD parameters may be specified after the PSD's name, and may be a maximum of 1024 characters long. The parameter string is not interpreted or parsed by OS/2, but is passed verbatim as an ASCIIZ string when the PSD's Install function is invoked.
If multiple PSD statements are encountered, OS/2 will load each PSD in the order listed in CONFIG.SYS, and call the PSD's install function. The first PSD which successfully installs will be the one OS/2 uses.
PSD statements are processed before BASEDEV, IFS, and DEVICE statements."
->\OS2\INSTALL\CAVERUN.PSD
->\OS2\INSTALL\OS2APIC.PSD
->\OS2\INSTALL\VIPERMP.PSD
->\OS2\INSTALL\EBI2.PSD
->\OS2\INSTALL\TRICRD.PSD
->\OS2\INSTALL\PROLIANT.PSD
->\OS2\INSTALL\WYSE.PSD
->\OS2\INSTALL\ALR.PSD
(The above are typical of middle of 1990's Compaq software bundle where OS/2 for SMP v2.11 was an option; notwithstanding, I believe that the maximum number of CPU/COREs supported was eight(8))
On OS/2 for SMP Version 2.11 Executing on 16 CPUs/Cores in VirtualBox We can Install HPFS386 File System Hack.
Shell
\AHPFS386.CMD |
(Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size. Alternatively, the video with larger screen size may be shown in the Calli, i.e., 'Home', collection front page)
Other Unix virtual file systems include the File System Switch in System V Release 3, the Generic File System in Ultrix, and the VFS in Linux. In OS/2 and Microsoft Windows, the virtual file system mechanism is called the Installable File System.
Wikipedia: Virtual File System
The Installable File System (IFS) is a filesystem API in MS-DOS/PC DOS 4.x, IBM OS/2 and Microsoft Windows that enables the operating system to recognize and load drivers for file systems.
...
The IFS provided a basic and powerful interface for programming filesystems. It was introduced in 1989 in OS/2 1.20, along with the HPFS filesystem.
Filesystem drivers executed in kernel-space (ring 0) and are divided in four principal pieces: microIFS, miniIFS, IFS, helpers.
Only the IFS and the filesystem code itself is required and it is loaded via an "IFS=" statement in the CONFIG.SYS file:
(For instance,)
ZipStream
iswas an OS/2 2.x Installable File System (IFS) that mirrors access to existing OS/2 File Systems and simultaneously provides automatic, transparent file compression and decompression.
...
Its 32 bit implementation exploits OS/2's pre-emptive multi-threaded processing capabilities, allowing complex processing to be carried out in an optimum manner.
The microIFS is a piece of code that loads in memory the kernel and the miniIFS and jumps to kernel execution. It is usually in the boot portion of the filesystem.
i.e.,
'Big Blue'... could make a minimum investment in virtualizing the OS/2 boot procedure with the Kernel-based Virtual Machine (KVM) Linux virtualization technology used extensively by Red Hat -- IBM's latest acquisition!
Tlacatecolotl: OS/2 for Symmetrical Multiprocessing(SMP) v2.11 HPFS386 on Headless VirtualBox 7.0.12
Wikipedia: Installable File System
For OS/2 two kinds of IFS drivers were available for HPFS file system:
- The standard one with a cache limited to 2 MB
- HPFS386 provided with certain server versions of OS/2, or as added component for the server versions that did not come with it.
HPFS386's cache is limited by the amount of available memory in OS/2's system memory arena[1] and was implemented in 32-bit assembly language. HPFS386 is a ring 0 driver (allowing direct hardware access and direct interaction with the kernel) with built-in SMB networking properties that are usable by various server daemons, whereas HPFS is a ring 3 driver. Thus, HPFS386 is faster than HPFS and highly optimized for server applications. It is also highly tunable by experienced administrators.
Wikipedia: High Performance File System
Here we have an OS/2 for SMP v2.11 with HPFS386 hack -- on 16 CPU/Cores/Threads in VirtualBox 7.1.6 -- running GammaTech GTDISK utilities and seemingly saying (to IBM), 'Look ma', my CPUs or Cores or Threads do not hang me!' ![]()
Typical OS/2 for SMP Version 2.11 CONFIG.SYS -- Installed to Drive H: -- Retrofitted with HPFS386 File System, MultiMedia, and TCP/IP
Here is some rearranged and enhanced code of A non-real-life example to prove a point1...
Unlike the initial preliminary hard-coded int 16 assigned to the variable threads, as elaborated at Ahuiani: OS/2 for Symmetrical Multiprocessing(SMP) v2.11 with HPFS386, MultiMedia, and TCP/IP stack., this version does query/detect the number of threads, as the original author intended. Further, it will output the int CPUs/COREs variable detected in OS/2.
Shell
#define INCL_DOSPROCESS | |
#define INCL_DOSMISC | |
#include <os2.h> | |
#include <stdio.h> | |
#include <time.h> | |
| |
#ifndef QSV_NUMPROCESSORS | |
/*The QSV_NUMPROCESSORS is only defined in the SMP toolkit, | |
*and since the SMP toolkit is always at least 6 months behind | |
*the normal toolkit you will probably not want use it. | |
*/ | |
#define QSV_NUMPROCESSORS 26 | |
#endif | |
| |
int GetNumberOfCPUs() { | |
ULONG CPUs; | |
APIRET rc; | |
CPUs = 0; | |
rc = DosQuerySysInfo(QSV_NUMPROCESSORS, | |
QSV_NUMPROCESSORS, | |
&CPUs, | |
sizeof(CPUs)); | |
/*We have to guard against running under a non-SMP OS/2 | |
*that does not support index 26, and that index 26 (as | |
*far as I remember) has previously been used for | |
*something else | |
*/ | |
| |
if(rc!=0 || CPUs<1 || CPUs>64) | |
CPUs = 1; | |
return CPUs; | |
| |
} | |
| |
void SpendTime(int howmuch) { | |
//Use some CPU time | |
// - and beg that your compiler does not optimize this aways | |
int x=0; | |
for(int i=0; i<howmuch; i++) { | |
x += 2; | |
} | |
} | |
| |
void APIENTRY MyThread(ULONG howmuch) { | |
SpendTime((int)howmuch); | |
DosExit(EXIT_THREAD,0); | |
} | |
| |
| |
int main(void) { | |
TID tid[64]; //array to hold the TIDs of the threads | |
int threads=GetNumberOfCPUs(); //how many threads to create | |
int howmuch=1000000000; | |
// int howmuch=1000000000000000000; | |
int t; | |
| |
clock_t starttime=clock(); | |
| |
//create threads | |
for(t=0; t<threads; t++) { | |
DosCreateThread(&tid[t], | |
MyThread, | |
(ULONG)(howmuch/threads), | |
CREATE_READY|STACK_COMMITTED, | |
8192 | |
); | |
} | |
| |
//wait for the threads to finish | |
for(t=0; t<threads; t++) { | |
DosWaitThread(&tid[t],DCWW_WAIT); | |
} | |
| |
clock_t endtime=clock(); | |
| |
printf("CPUs/COREs detected: %d", threads); | |
printf("\nRunning time: %f seconds\n", ((double)(endtime-starttime))/CLK_TCK); | |
| |
return 0; | |
} |
Example SMP_OME executable program OS211-SMP_OME.ZIP is available AS-IS, i.e., no explicit nor implicit warranties and whoever downloads it s/he/they do at their own discretion. (Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size. Alternatively, the video with larger screen size may be shown in the Calli, i.e., 'Home', collection front page)
OS/2 for SMP Version 2.11 with HPFS386 hack, MultiMedia, and TCP/IP Version 2.04 in Action!
After installing the TCP/IP v2.x stack and its fixpak UN64092,
OS/2 for SMP Version 2.11, with HPFS386 file system hack and multimedia, can still implement The Network is the Computer protocols, as shown by pinging a couple of sites and -- provided we install the IBM WebExplorer v1.01 -- browsing a few still compatible sites.
---
NOTE: If you want to acquire this OS/2 2.11 SMP Bootable CD/ISO image hack, it comes in a bottle opener USB stick:
and includes the IBM base OS/2 2.10 CDROM image on which the hack was loosely based.
REFERENCES:
1 EDM/2 SMP - Symmetrical Multiprocessing
CAVEAT: I have seen some videos/statements out there where the OS2APIC.PSD is simply extracted from a higher version OS/2 for SMP and rammed in with an OS2KRNL with none or limited support for SMP, i.e., a two- CPU/Core OSKRNL with a Warp 3 server (vanilla or Advanced), Warp 4, and/or WSeB, -donated OS2APIC.PSD being presented as an four(4) CPU/CORE SMP in a YT video out there (hint ![]() . Well, yes, the pseudo- SMP OS/2 will experience frequent severe locks during execution.
. Well, yes, the pseudo- SMP OS/2 will experience frequent severe locks during execution. ![]() Yet, the narrator will blame those events on legacy OS/2 SMP 'instability' thus cloaking his/her technical deficiency instead of admitting that s/he is cheating -- making fraudulent claims to defame the legacy OS/2 technology! i.e., YT video fragment:
Yet, the narrator will blame those events on legacy OS/2 SMP 'instability' thus cloaking his/her technical deficiency instead of admitting that s/he is cheating -- making fraudulent claims to defame the legacy OS/2 technology! i.e., YT video fragment:
Ольга Пронина (Monika9422) её видео
'One of the biggest advantages of my hobby is that a motorbike disciplines you. Thanks to him, I'm in perfect physical shape because motorbikes are not for weak women.'~ Olga spoke in her blog of her motorbike as if it was a person1
Subsequent her tragic death, I had posted her video to one of fascist 'Murika's censorship...er, 'social,' media platforms. Recently, however, I came across it in my local storage media and... well, here it is:
References:
1 Queen of bikers killed in horrific crash leaving her teenage daughter motherless

Hacking an OS/2 2.1 Floppy Set or CDROM Into a Bootable CDROM Media / ISO Image
(Once the video player has started, right selecting (or 'clicking') your device (or 'mouse') will show menu option, 'Open video in new tab', which will enable larger screen size. Alternatively, the video with larger screen size is shown in the Calli collection front page)
Although IBM OS/2 3.x Warp and higher indigitalizations have been hacked into bootable CDROM media / ISO images, I believe this is the first OS/2 2.x which has been morphed into such an unique entity. The procedure was not easy -- and obviously not intuitive. The work required to make the cdboot hack complete the first phase of the OS/2 2.1 installation was substantial; and once I achieved it I thought that whatever else needed to be done would be easier. I was mistaken. I had to compile an utility to search for and replace strings in the OS/2 2.1 CONFIG.SYS file at the end of the first phase of the OS/2 installation. Fact is, I could not find an appropriate binary one which executed under OS/2 2.1x in my extensive local collection of Hobbes CDROM media, etc., nor online at Hobbes site ![]() sun set and/or elsewhere.
sun set and/or elsewhere.
At the time I used the IBM C/C++ Tools 2.01:
to build the STRRPL.EXE utility which source code was freely available:
Unlike prebuilt STRRPL.EXE binary from strrpl_0-84r2.zip available from Hobbes static archive, and elsewhere,
my build of STRRPL.EXE with IBM C/C++ Tools 2.01 actually executed under OS/2 2.1x:
Accordingly, I repackaged the original strrpl_0-84r2.zip as strrpl_0-84r2m.zip and under OS2v21/ directory included the binary executable strrpl.exe which does function properly under OS/2 v2.x
Had IBM released the OS/2 code as free and/or open source software (FOSS) instead of being so indifferent to the multiple petitions to do so (for instance those in which I personally took part at the OS2World site before I left the site for good -- as I had moved on to GNU/Linux Debian) the avaricious plutocrat Bill Gates' mediocre 'creation', backdoored software, idiotically named as a mundane household notion, 'windows,' would not have spread like the virus it emulates.
Generating an OS/2 2.1x bootable CD under GNU/Linux Debian -based Metztli Reiser4:
Shell
genisoimage -r -b boot/boot.img -c boot/boot.catalog -o os2bootcd.iso . |
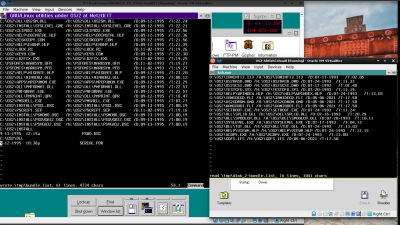
Ensuing snapshot is an specific example of the above command under my Metztli Reiser4 Debian environment, where my two(2)-floppy boot.img is custom-renamed as bootsmphpfs386.img and os2bootcd.iso is written to another directory -- relative to our current position in the shell -- and custom renamed, too:
The layout in the snapshot 'a priori' shows multi-media and tcpip, and their corresponding update suffixes: u1, u2, and upd. That is what you get when you acquire either of the OS/2 v2.11 for Symmetrical Multiprocessing with HPFS386 hack that I have on sale.../xicnahualti_hpfs386-caxtolli_omome/os211smphpfs386metztli.iso
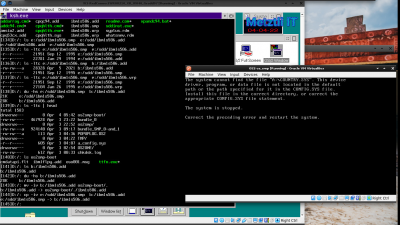
Generally speaking, even if your bootable two(2) disk image is successfully created, if it can not make the transition to the OS/2 disks layout on the CD, i.e., can not detect it due an older driver like IBM1S506.ADD (see snapshot below), the boot procedure will stop with the output:
The system cannot find the file "A:\COUNTRY.SYS". This device driver, program, or data file is not located in the default path or the path specified for it in the CONFIG.SYS file. Install this file in the correct directory, or correct the appropriate CONFIG.SYS file statement.
The system is stopped.
Correct the preceding error and restart the system.
Shell
cmd /c "PACK bundle.list bundle /L" |
If, unlike myself, you are not using the Korn Shell under OS/2, then the command delimited by double quotes is sufficient.
CONVERT FROM 2.1 BASE VIDEO INTO 3.0 BASE VIDEO IN ORDER TO TAKE ADVANTAGE OF THE MONITOR CONFIGURATION FEATURE OF THE 3.0 SYSTEM ICON
- Hint 4)
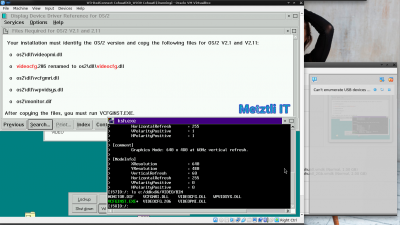
Display driver reference lists the binary files that compose the base video subsystem and explains the difference in the installation between 3.0 and 2.1. Search for VIDEOCFG to see all references. - i.e.,
MONITOR.DIF
VCFGINST.EXE
VCFGMRI.DLL
VIDEOCFG.206 (To be renamed as VIDEOCFG.DLL when copied over to OS/2 v2.11)
VIDEOCFG.DLL (This is for OS/2 Warp 3)
VIDEOPMI.DLL
WPVIDSYS.DLL
Dual-booting with OS/2 for SMP v2.11 and Warp 3 Connect Uni-Processor.
Caveat: If using a single CPU/CORE, then the CONFIG.SYS FOR OS/2 for SMP v2.11 must have disabled the statement
PSD=OS2APIC.PSD /APIC
i.e.,
REM PSD=OS2APIC.PSD /APIC
else, it will not dual-boot with an OS/2 Uni-Processor in a VirtualBox 7.0.14 (currently being used).
REFERENCES:
Creating bootable CD-ROMs
(work in progress)






















Recent comments: